NewComplete application redesign
NTFS reporting with
Permission Analyzer
Combines NTFS file permissions with user and group data from the Active Directory. Scan once, and run your overviews in seconds using a dedicated database instead of the file system.
No installation required, just unzip!
- Query a database instead of network shares
- Create user segments, include nested group memberships, and find the origin of permissions
- Schedule HTML/CSV reports and define audit policies with alert notifications
- NEW: Compare HTML/CSV reports and track changes



Trusted Over 1000+ Companies

Security National Bank
Security National Corporation, a multi-bank holding company, owns Security National Bank in Sioux City, Akron, and Mapleton, Iowa. Today, Security National Bank is the largest locally owned bank in Sioux City, Iowa.


United State Air Force
The U.S. Air Force is a military service branch organized within the Department of the Air Force, one of the three military departments of the Department of Defense.


Patriot Forge
Patriot Forge Co. is the largest custom open-die forging company in Canada and a leader in the Global market.


National Bank Kyrgyz Republic
The overall objective of the activity of the National Bank of the Kyrgyz Republic is to achieve and maintain stability of prices by means of implementing an appropriate monetary policy.


RSA Insurance Co
With a 300 year heritage, RSA is one of the world’s leading multinational quoted insurance groups.


UK Coal PLC
The largest producer of coal in the UK and a significant supplier to the electricity industry.


CIVCO Medical Solutions
CIVCO Medical Solutions is committed to positively impacting patient care by constantly innovating life enhancing medical solutions.


Talpa Media Holding b.v.
Talpa Media comprises Talpa Netherlands and Talpa Global. Talpa Global is dedicated to the worldwide licensing of Talpa Content’s formats and finished series.


Standard Chartered Bank
Korea international bank and the largest foreign investor in Korea’s financial service industry.


St. Bernards Healthcare
St. Bernards Medical Center is the healthcare destination for families in Jonesboro and the surrounding areas. It provides secure, confidential web-based access to your medical records.


WILDGEN
Partners in Law, one of the best known and well-respected law firms in Luxembourg.


Centaur Media
Centaur Media creates expert content and insight, engaging events and smart digital technology.


UCAN
UCAN serves 10,000 at-risk children across Illinois through more than 30 programs that create a healing process for youth who have experienced trauma.


Cyient
Creates and delivers services that enhance your business agility. Has more than 12,900 associates across 36 global locations, with delivery centers in North America, Europe, the Middle East and Asia Pacific.


KD Engineering
KD Engineering Co. supports the needs of T.A.B. (Testing, Adjusting and Balancing) services within British Columbia.


Timberlands Ltd
TIMBERLANDS Limited is a forest management company, who acts on behalf of owners of significantly large forest estates, in order to grow cash return, generate the most value from their forest investment and protect their asset.


Excelsior College
Excelsior College provides educational opportunity to adult learners with an emphasis on those historically underrepresented in higher education.

Permission Analyzer
Get in control!
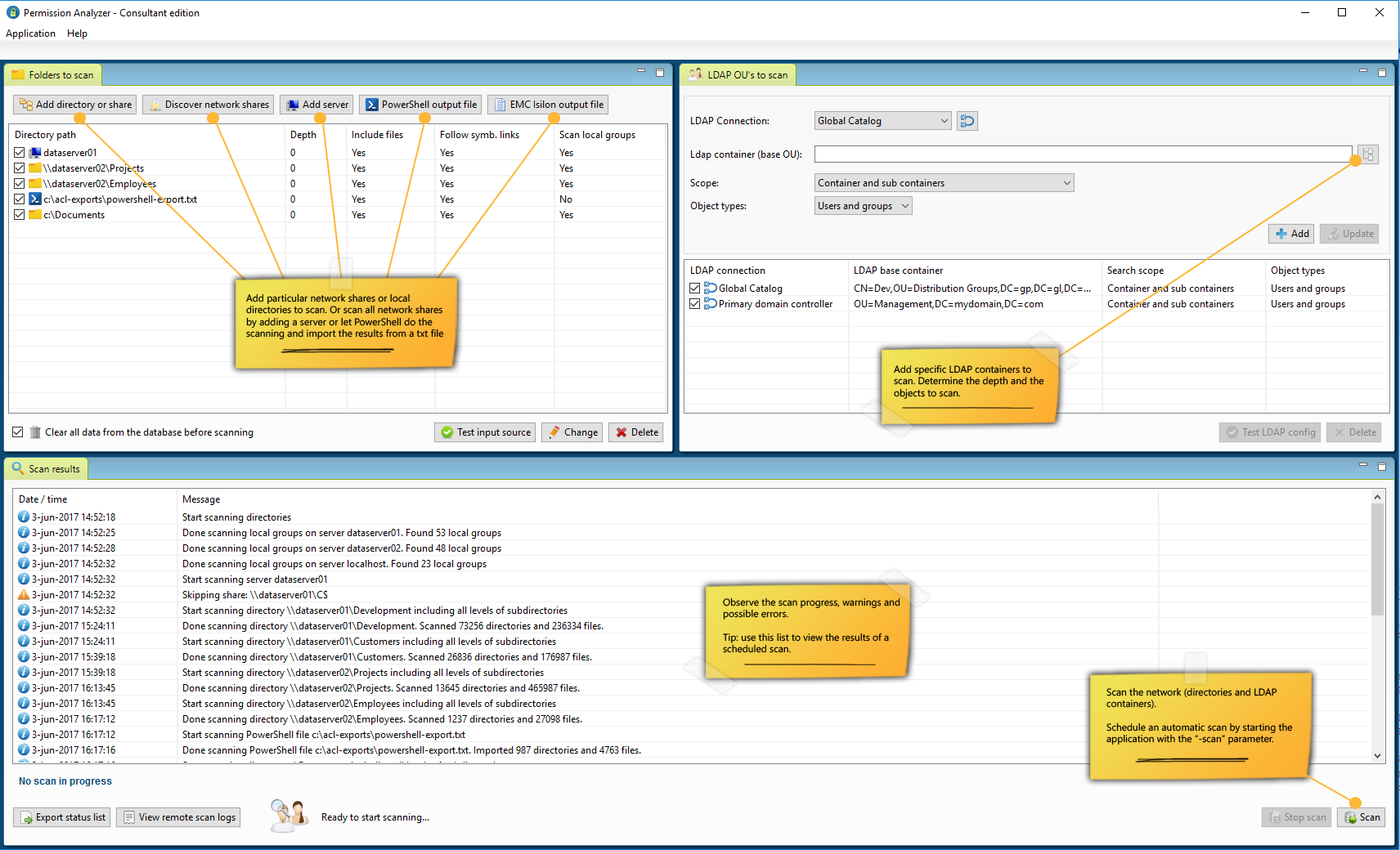
Scan your network
NTFS permissions and group memberships from Active Directory are saved in a embedded or remote database. Run the scan whenever you like or schedule an automated scan. Permission Analyzer supports an external database, allowing multiple workstations to share the same information source.
Learn More
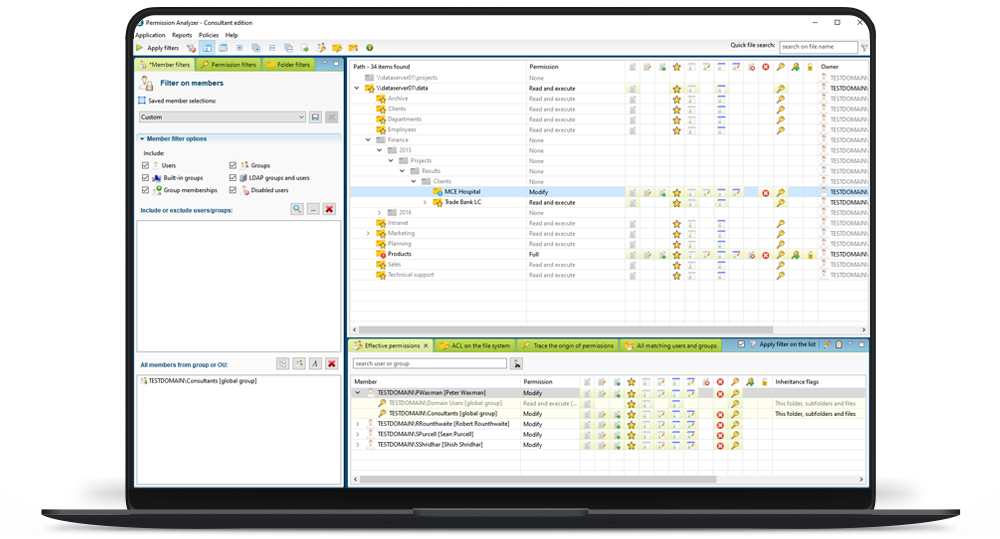
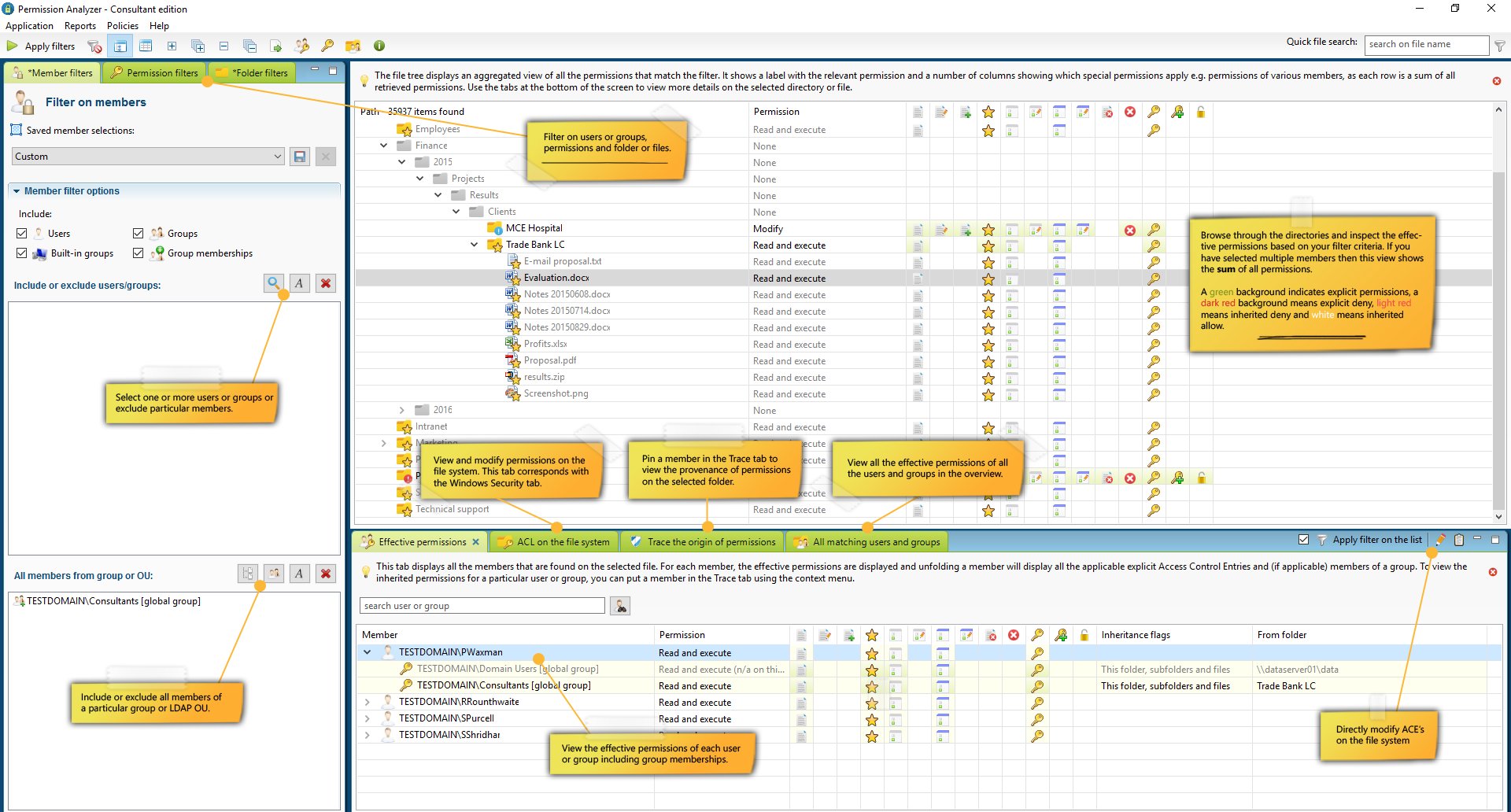
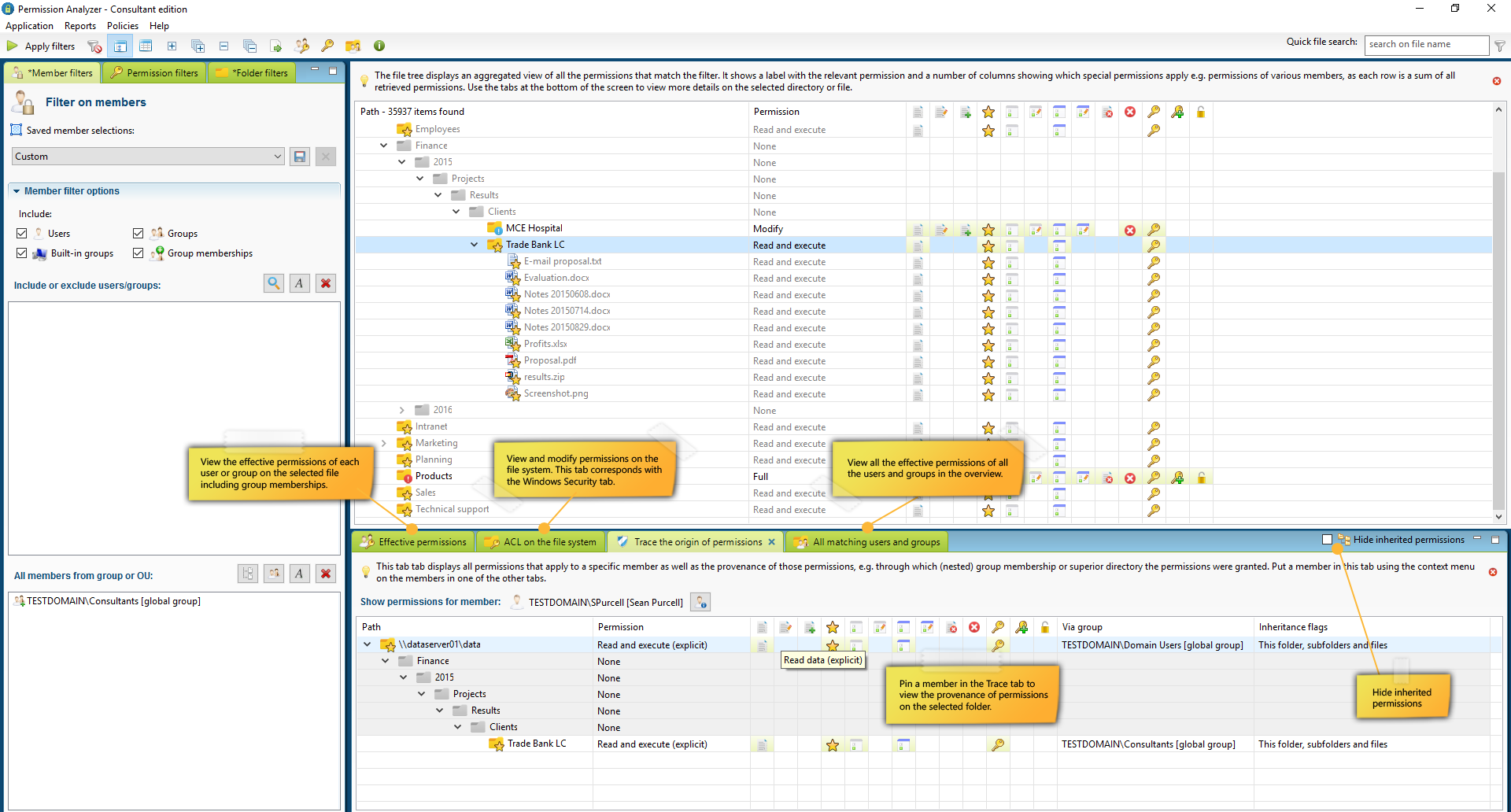
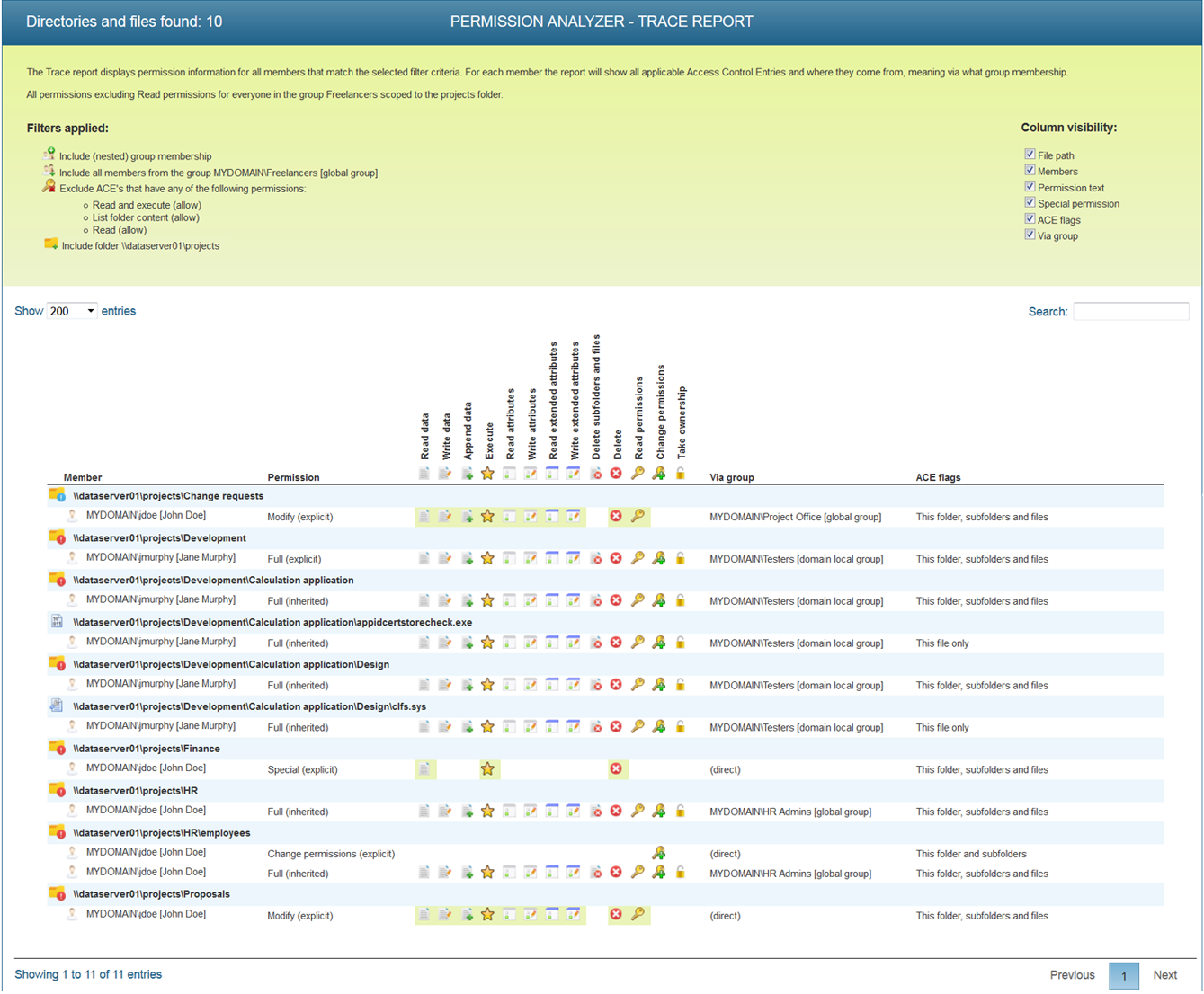
Check your NTFS permissions
Conduct targeted search queries in seconds, instead of scanning the whole network every time you want to apply a new filter. Use your filters to check for unwanted permissions, including the nested group memberships of every member in your selection!
Learn More
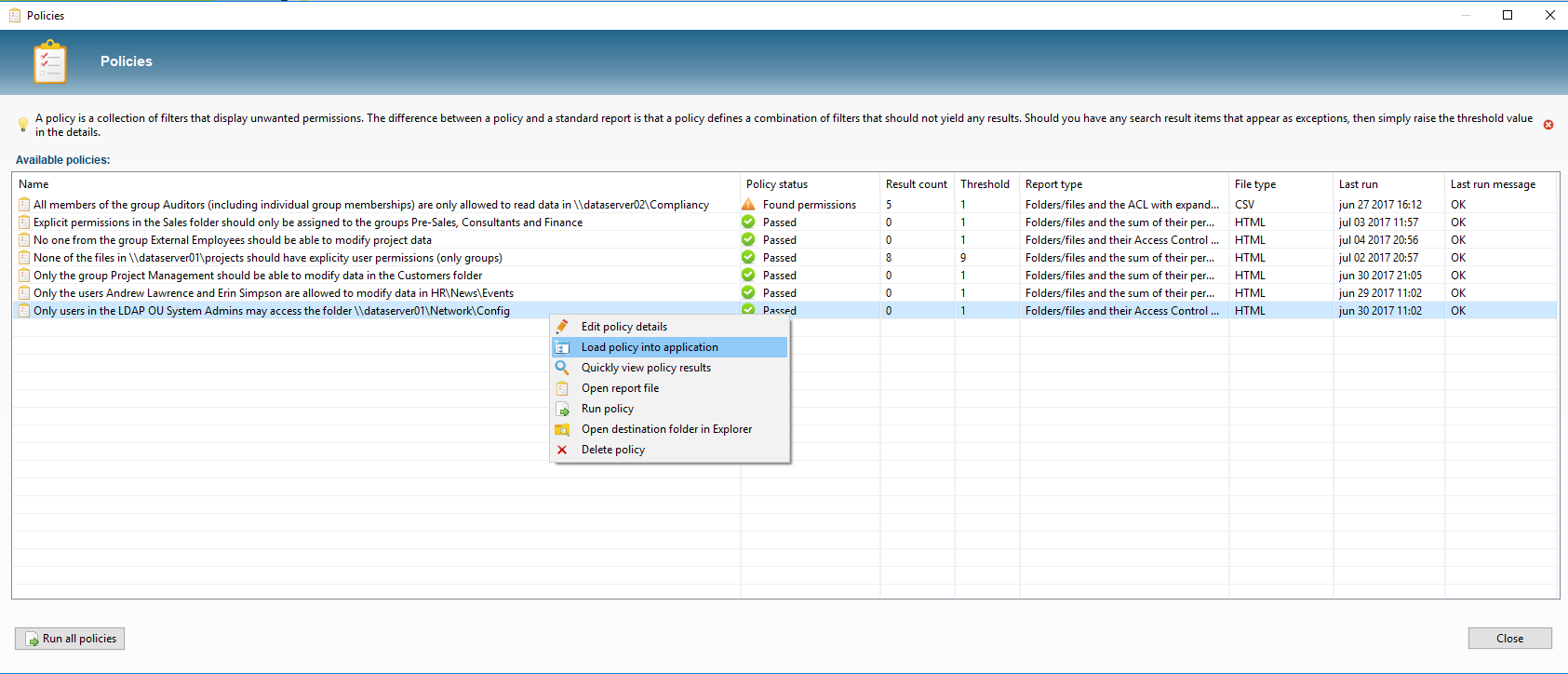
Export to HTML reports
Save your filters as report and export them to HTML or CSV and e-mail. Export your reports automatically using command-line parameters. Save your filters as audit policies and only receive e-mail notifications if your policy report contains new unwanted permissions!
Learn More

See for yourself!
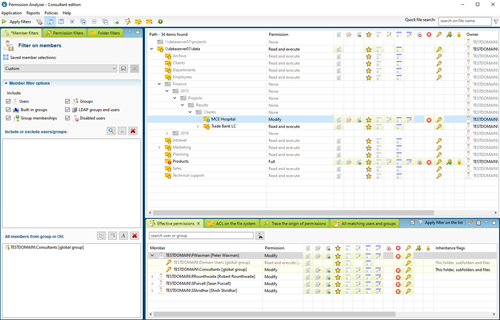
Find out what NTFS permissions are currently in your network! All data is stored in a local or remote database and can be utilized to create overviews of permissions based on many filter criteria. You will be able to monitor permissions for entire user groups and receive notifications if undesired permissions are found within your network.
- Query a database instead of network shares
- Support for many filters, including nested group memberships
- Different views to zoom in on the results
- Schedule HTML reports
- Define policies and receive e-mail alerts
Our features
Why you choose Permission Analyzer
Scanning the file system and AD
Specify directories, network shares or server names to scan and configure depth. Select particular AD Organizational Units to scan.
Filters and overviews
Create filters and include or exclude particular members, simple or special permissions and folders or files. Save your filters as Selection or save and re-use them as report.
Tracing permissions
Zoom in on your search results and trace the origin of permissions that have been found. See if permissions are inherited from a (indirect) group membership or parent folder.
Reports and export
Save your filters as report and export them to HTML or CSV and e-mail. Use different report types, such as permissions tracing and group memberships, effective permissions or plain Access Control List information of your directories. Compare past reports and track changes!.
Defining audit policies
Save your filters as policies and receive e-mail notifications if your policy report contains unwanted permissions.
Scheduling jobs
Use command-line parameters to run a network scan or report export automatically. Let Permission Analyzer check all your policies and send out e-mail notifications by running the application with parameters and Windows Scheduler.
Modifying permissions
Change the permissions of a directory directly from within the application. Changes are directly applied to the file system and the database is updated with the changes made.
Data protection
Permission Analyzer can be secured with an application password. The password is required to open up the application and may be used to encrypt the local database using strong AES encryption.
External database
Permission Analyzer is supplied with an embedded database to store directory and group membership information. It supports a central company database, so that workstations can use the same information source or so you can create your own queries and integration.
Testimonial
What our customers are saying
We needed an overview of all the access rights in our network. I am now able to run reports to give to the department director so that they can see who has what permissions and to either add or remove users. This is what I am truly after. Permission Analyzer helps me by doing the initial scan and letting me know what is out there now.
E. Martin
An ECR International spokespersonWe are currently trying to analyze our user rights on the network, but have not found a tool that displays easy-to-read report data. I have downloaded your demo and have found it much easier to use, and seems much faster than Hyena when it comes to collecting data from our servers.
C. North
Park CommunityI have been looking for just this type of tool to use in the many conversions and acquisitions that we are involved with. Some small and some very large.
K. Hoggatt
HP Enterprise ServicesI ran the program and I liked it; I think it will work for what I need which is to find out who has what permissions, and where.
Brad R. Willett
United States Air ForceThank you it is looking correct now. I would like to say the support from you has been fantastic!! Thank you very much. I will be strongly recommending this software to any organisation requiring high security around folders permissions.